Red Team Confluence Wiki
Core Concept
Red Team
A Red Team is a group of security professionals that simulate real-world adversaries to test an organization’s security posture. Unlike traditional security testing, Red Teaming is goal-oriented, often aiming to achieve objectives such as data exfiltration, domain dominance, or persistent access while avoiding detection.
Key Characteristics:
-
Adversary Emulation: Mimics specific threat actors, their tactics, techniques, and procedures (TTPs).
-
Full-Scope Testing: Includes social engineering, physical security, network exploitation, and more.
-
Focus on Evasion: Red Teams attempt to bypass security controls and operate undetected.
-
Real-World Attack Scenarios: Unlike vulnerability assessments or penetration tests, Red Teaming tests detection and response capabilities.
Red Team vs Penetration Test vs Vulnerability Assessment
Red Team Assessment: A goal-based adversarial simulation that emulates a real-world attack using the full spectrum of TTPs against all organizational attack surfaces (technical, physical, social) to test detection and response capabilities. It focuses on achieving specific objectives while avoiding detection.
Penetration Test: A focused technical assessment that identifies and exploits vulnerabilities in specific systems, networks, or applications to determine their exploitability and potential impact. It aims to find and validate as many vulnerabilities as possible within a defined scope.
Vulnerability Assessment: A systematic review to identify, classify, and prioritize vulnerabilities in systems, applications, and network infrastructure. It focuses on discovery and documentation without actually exploiting the vulnerabilities.
| Feature | Red Teaming | Penetration Testing | Vulnerability Assessment |
|---|---|---|---|
| Objective | Simulate a real-world adversary attack | Identify and exploit security weaknesses | Identify vulnerabilities and misconfigurations |
| Scope | Broad, covers multiple attack vectors | Focused on specific systems/applications | Comprehensive review of vulnerabilities |
| Methodology | Adversary tactics, stealth, long-term persistence | Exploit known vulnerabilities to gain access | Identify and report vulnerabilities without exploitation |
| Testing Approach | Full-scope (physical, cyber, social engineering) | Controlled environment, usually black/gray box | Automated and manual scanning |
| Timeframe | Weeks to months | Days to weeks | Typically a short-term engagement |
| Stealth Required? | Yes, must avoid detection | No, detection not a primary concern | No, focuses on identification |
| Security Team Involvement | Tests Blue Team’s response & SOC capabilities | Security team may or may not be aware | Security team involved in patching |
| Deliverables | Executive report, technical findings, MITRE ATT&CK mapping | List of exploitable vulnerabilities, risk ratings | List of vulnerabilities, risk scores, recommendations |
| Best For | Testing an organization's full security maturity | Assessing security posture of specific assets | Continuous vulnerability management |
OPSEC
OPSEC is a process that identifies critical information to determine if actions can be observed by adversaries, determines if information obtained by adversaries could be harmful, and then executes measures to eliminate or reduce vulnerabilities.
In red teaming, OPSEC refers to the practices and procedures used by the red team to protect their activities from detection by the blue team or other security monitoring systems. This includes:
- Infrastructure compartmentalization: Separating attack infrastructure to minimize correlation and attribution
- Communication security: Using encrypted and out-of-band channels for team communications
- Attribution obfuscation: Masking the true source of attacks
- Traffic patterns management: Ensuring red team activities mimic expected patterns or blend with normal traffic
- Tool selection and modification: Using custom tools or modifying existing ones to avoid signature detection
- Operational tradecraft: Methodologies to minimize digital footprints and artifacts
- Data sanitization: Removing identifying metadata from files and communications
Proper OPSEC is crucial for red teams as premature detection can invalidate assessment results and fail to accurately test the organization's true detection capabilities.
Attack Life Cycle
The attack lifecycle refers to the phases an adversary follows to achieve their objective, such as initial access, privilege escalation, lateral movement, and exfiltration. Various cybersecurity frameworks outline these steps:
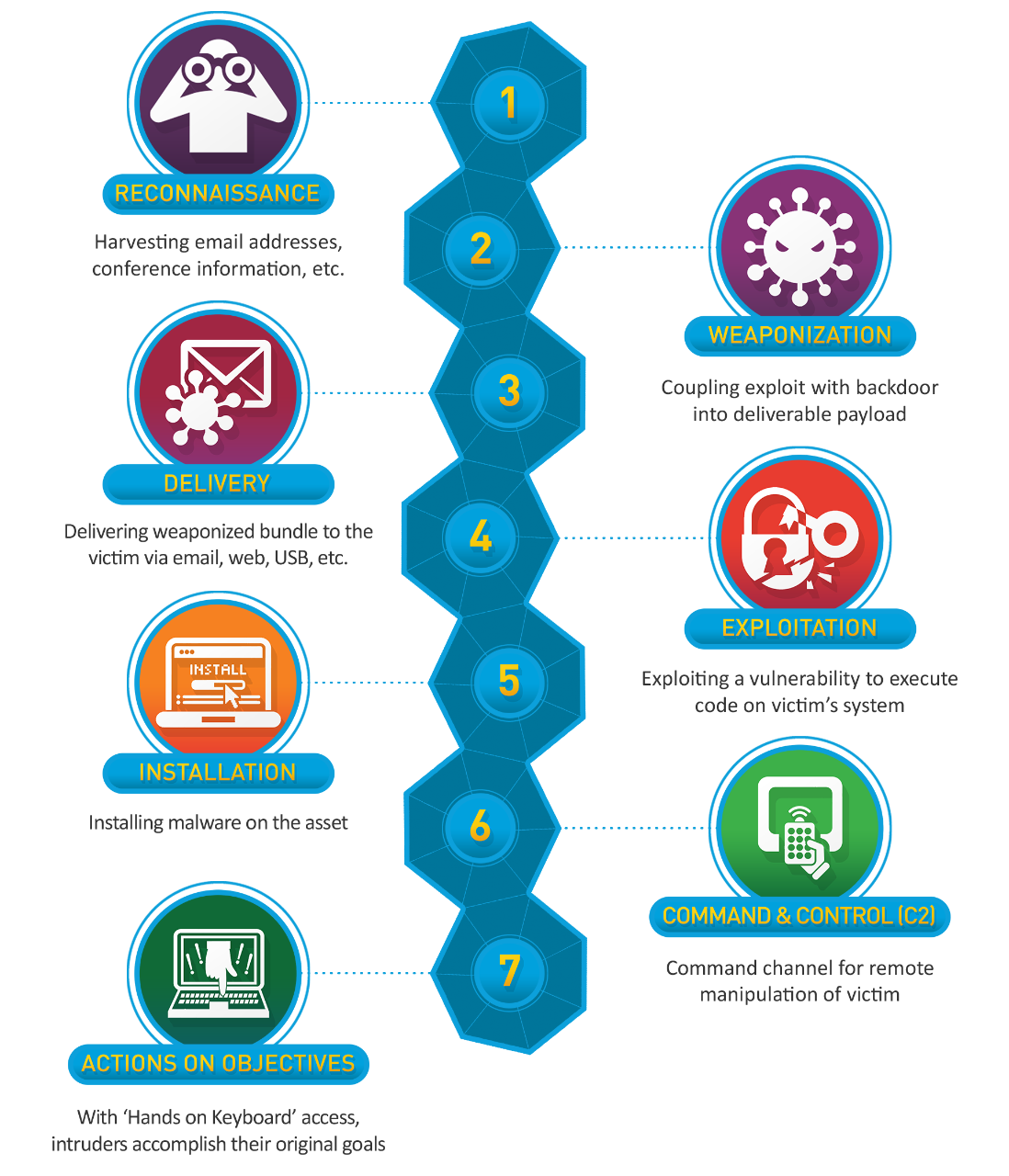
1. Cyber Kill Chain (Lockheed Martin)
Attack life cycles are models that describe the sequence of steps attackers typically follow when compromising an organization.
Cyber Kill Chain (Lockheed Martin)
A 7-stage model describing the structure of an attack:
- Reconnaissance: Gathering information about the target
- Weaponization: Coupling exploits with backdoors into deliverable payloads
- Delivery: Transmitting the weapon to the target environment
- Exploitation: Triggering the attacker's code in the target environment
- Installation: Installing malware or backdoor on the asset
- Command & Control (C2): Establishing persistent remote control over the victim
- Actions on Objectives: Executing the intended goals of the intrusion
Mandiant's Attack Lifecycle (now expanded to 8 phases)
Describes how targeted attacks unfold:
- Initial Reconnaissance: Identifying targets and gathering intelligence
- Initial Compromise: First breach of the target environment
- Establish Foothold: Setting up persistent access
- Escalate Privileges: Obtaining higher-level permissions
- Internal Reconnaissance: Mapping the internal environment
- Lateral Movement: Moving through the network to reach objectives
- Maintain Presence: Ensuring continued access
- Complete Mission: Achieving the attack objective (data exfiltration, destruction, etc.)
Red teams use these models to structure their activities and ensure their simulations accurately reflect real-world attack methodologies. They also provide a framework for organizations to understand where they need to implement defensive controls.
Engagement Planning
Engagement Planning is the systematic process of preparing for a red team operation. It creates the foundation for the engagement's success and ensures alignment with organizational objectives. Key components include:
- Scope Definition:
- Clearly defining technical boundaries (networks, systems, applications)
- Identifying physical locations included in testing
- Determining if social engineering is permitted
- Establishing excluded systems (e.g., production-critical infrastructure)
- Threat Modeling:
- Identifying relevant threat actors based on industry, geography, and data types
- Researching TTPs of selected adversaries
- Mapping potential attack surfaces to threat capabilities
- Prioritizing likely attack vectors
- Breach Model:
- Determining the initial access scenario (e.g., external attacker, malicious insider)
- Defining assumed breach parameters if applicable
- Establishing initial access limitations or advantages
- Notification & Announcement:
- Determining who will be aware of the exercise (full knowledge, limited knowledge, no knowledge)
- Creating communication templates for stakeholders
- Establishing emergency notification procedures
- Planning for potential business disruption communications
- Rules of Engagement (ROE):
- Documenting permitted and prohibited techniques
- Defining operational hours and blackout periods
- Establishing approval processes for high-risk activities
- Creating escalation procedures for security incidents
- Identifying points of contact for various scenarios
- Record Keeping & Deconfliction:
- Establishing logging requirements for all team activities
- Creating protocols to avoid conflicts with other security testing
- Implementing change management procedures
- Setting up communication channels with security operations
- Data Handling:
- Defining protocols for sensitive data discovery and handling
- Establishing secure storage for engagement artifacts
- Creating data destruction procedures post-engagement
- Implementing encryption requirements for team communications
- Duration:
- Setting timeframes for different phases (planning, execution, reporting)
- Establishing milestones and checkpoints
- Planning for potential extensions based on findings
- Resource Costs:
- Team composition and personnel requirements
- Hardware and infrastructure needs
- Software licensing and tooling costs
- External service requirements (VPS, domains, etc.)
- Training or specialized skill acquisition
Effective engagement planning ensures the red team assessment delivers maximum value while minimizing operational risks and unintended consequences.
Post-Engagement and Reporting
Post-Engagement and Reporting refers to the activities following the active testing phase of a red team engagement. This phase is critical for translating the technical findings into actionable intelligence and value for the organization. Key components include:
- Evidence Collection and Preservation: Compiling and organizing all data, screenshots, logs, and artifacts gathered during the engagement
- Attack Path Reconstruction: Documenting the complete attack chains from initial access to objective completion
- Attack Narratives:
- Chronological storytelling of the attack progression
- Detailed walkthroughs of successful attack paths
- Description of attempted but unsuccessful approaches
- Mapping of techniques to the ATT&CK framework
- Explanation of how defenses were bypassed or triggered
- Finding Classification: Categorizing issues by severity, exploitability, and potential business impact
- Root Cause Analysis: Identifying underlying security weaknesses beyond individual vulnerabilities
- Recommendations:
- Strategic improvements to security architecture
- Tactical changes to configurations and controls
- Procedural enhancements for detection and response
- Prioritized remediation guidance based on risk
- Implementation difficulty ratings for suggested fixes
- Validation methods to confirm successful remediation
- Indicators of Compromise (IoCs):
- File hashes for tools and payloads used
- Network indicators (IPs, domains, URLs)
- Host-based artifacts and forensic evidence
- Registry keys and configuration changes
- Command line parameters and scripts
- YARA or Sigma rules for detection
- Report Development:
- Executive Summary: High-level overview of findings and implications for leadership
- Technical Report: Detailed documentation of methodologies, findings, and technical details
- Metrics and Scorecards: Quantitative measures of security posture
- Debrief Sessions: Presenting findings to different stakeholders:
- Executive briefing for leadership
- Technical debrief for security teams
- Purple team sessions with defenders to review detection gaps
- Remediation Support: Providing guidance during the fixing of identified issues
Effective post-engagement activities and reporting transform the red team exercise from a point-in-time assessment to a catalyst for lasting security improvements.
TTP
TTPs are the patterns of activities and methods associated with specific threat actors or groups of threat actors. They represent how attackers operate and provide a framework for understanding, documenting, and communicating about attacker methodologies.
- Tactics: The high-level description of an attacker's objective or goal. Tactics represent the "why" of an attack technique (e.g., initial access, privilege escalation, lateral movement).
- Techniques: The specific methods used by adversaries to achieve tactical goals. Techniques represent the "how" of an attack (e.g., spear phishing, pass-the-hash, living off the land).
- Procedures: The detailed implementation of techniques. Procedures represent the exact steps, tools, and operational practices that adversaries use when executing techniques (e.g., specific malware variants, particular command sequences, custom scripts).
TTPs are important in red teaming for several reasons:
- They enable realistic emulation of specific threat actors relevant to the organization
- They provide a common language for describing attack methodologies
- They help organizations prioritize defenses based on actual attack patterns
- They allow for mapping of defensive controls to specific adversary behaviors
Red teams select and implement TTPs based on threat intelligence about adversaries targeting the organization's industry or geographic region, creating more realistic and valuable security assessments.
ATT&CK
MITRE ATT&CK is a globally-accessible knowledge base and framework that catalogs adversary tactics and techniques based on real-world observations. It serves as a comprehensive, structured representation of attacker behaviors, spanning the entire attack lifecycle.
Key characteristics of the ATT&CK framework:
- Structure: Organized hierarchically into Tactics (categories of technical objectives), Techniques (methods to achieve tactical goals), and Sub-techniques (specific implementations of techniques)
- Matrices: Different matrices for various environments:
- Enterprise (Windows, macOS, Linux)
- Mobile (iOS, Android)
- ICS (Industrial Control Systems)
- Cloud (AWS, Azure, GCP, SaaS)
- Additional Components:
- Groups: Known threat actors and their associated TTPs
- Software: Tools, malware, and utilities used by threat actors
- Mitigations: Defensive measures mapped to specific techniques
- Data Sources: Telemetry types useful for detecting techniques
- Use in Red Teaming:
- Provides a common vocabulary for describing attack behaviors
- Enables creation of threat-informed scenarios based on real adversaries
- Facilitates documentation of testing coverage and gaps
- Allows mapping of defensive capabilities to specific attack techniques
- Supports reporting that connects findings to real-world threat behaviors
ATT&CK has become the de facto standard for describing adversary behavior in the security industry. Red teams use it to plan, execute, and document their operations, ensuring assessments are grounded in real-world attack methodologies and providing organizations with actionable intelligence about their security posture relative to actual threats.
External Reconnaissance
OSINT
DNS
whois
Social Media
Official Website
Passive Subdomain Enumeration
Dorking
Active Reconnaissance
Port Scan
Directory Bruteforce
Initial Access
Password-based Attack
Phishing
Exploit Public-facing Service
Valid Account
Supply Chain Pollution