Reuniting with a Childhood Friend Lost for 8 Years Using OSINT
OSINT,即开源情报,是网络安全领域中一项重要的技能。不仅是网络安全,情报界也广泛使用。对于网络安全人员,无论从事红队,还是蓝队,还是威胁狩猎/情报等,OSINT, or Open Source Intelligence, is a crucial skill in the field of cybersecurity. It is widely used not only in cybersecurity but also in the intelligence community. For cybersecurity professionals, whether involved in red teaming, blue teaming, or threat hunting/intelligence, OSINT 都能发挥不同的作用。对于红队来说,plays various roles. For red teams, OSINT 可以帮助操作员们在不与目标积极交互helps operators understand a target's attack surface and exposed vulnerable assets without actively interacting with the target (漏洞扫描,目录爆破,社会工程学尝试等such as vulnerability scanning, directory brute-forcing, social engineering attempts, etc.)的情况下了解目标的攻击面,掌握暴露的脆弱资产。对于蓝队以及威胁狩猎等更加偏向于主动与被动防御的角色来说,. For blue teams, threat hunter, and other roles focused on proactive or passive defense, OSINT 可以帮助工程师们识别攻击者的技术栈,个人信息,基础设施,背后势力等。can assist engineers in identifying attackers' technology stacks, personal information, attacking infrastructure, and the forces behind them.
作为一名红队操作员,在日常工作里,我主要利用As a red team operator, I primarily use OSINT 在侦察阶段尽可能获取目标更多的攻击面,脆弱资产,人员信息等,即为进攻性安全服务。而今天,我想分享一个不是那么进攻性,能带来温暖和感动的during the reconnaissance phase to gather as much information as possible on the target’s attack surface, vulnerable assets, and personnel, all aimed at offensive security purposes. However, today I want to share a case that is not so much about offensive security, but rather a heartwarming example of how OSINT 案例。我帮助了一位学妹和朋友,主要凭借着她提供的姓名,联系到了失去联络can 8bring 年之久的年少时的亲密伙伴。warmth and emotion. I helped a junior schoolmate and friend reconnect with a childhood companion whom she had lost touch with for over eight years, relying primarily on the name she provided.
在茫茫互联网中寻找一位特定的人,Finding a specific person on the vast internet with OSINT 绝不只是在involves far more than simply searching for specific keywords on Google 等搜索引擎中检索特定的关键字,毕竟这谁都会,没有技术含量可言。or other search engines—anyone can do that, and it lacks technical sophistication. OSINT 需要我们精炼已有的信息,对信息设置不同的优先级与重要性,对信息进行发散,对海量的信息筛选和过滤等。一些常见的技术有:搜索引擎的高级搜索,各类requires Dorking,关键字变种与迁移,利用在线工具与us API,社交媒体检索,文件元数据提取,泄露数据查询,研究目标可能的人脉和圈子等。to refine existing information, prioritize it by importance, expand upon it, and sift through and filter massive amounts of data. Some common techniques include advanced search engine queries, various dorking techniques, keyword variations and expansions, using online tools and APIs, social media searches, extracting metadata from files, querying breached data, and investigating the target’s possible connections and social circles.
Motivation and Background
作为一名网络安全从业人员,我一直希望能熟练掌握与应用一些既能在工作中大放异彩,也能在生活中实用的技术。你说攻击一个网站,挖掘软件的漏洞?算了吧,这很酷但不够实用。能让我想到的一些技术有:撬锁,As a cybersecurity professional, I've always aspired to master and apply certain skills that not only shine at work but also prove useful in everyday life. Hacking a website or discovering software vulnerabilities? Sure, it's cool, but not very practical for daily use. The skills that come to mind are things like lock-picking, using tools like the Flipper ZeroZero, 的一些使用,OSINT。我在上文说了,and, of course, OSINT. As I mentioned earlier, OSINT 被多个领域所运用。网络安全之外,有一些内容创作者会挑战自己从一张看似普通的图片中提取大量的信息,最终得到例如图片中风景所在的地理位置,呼啸而过的列车的编号,几行模糊的文字所在的书籍。还有一些账号会追踪一些名人的踪迹,例如:is utilized in many fields beyond cybersecurity.
Outside of cybersecurity, some content creators challenge themselves by extracting a wealth of information from what seems to be an ordinary image. They can deduce details such as the geographic location of the landscape in the picture, the identification number of a passing train, or even the book to which a few blurry lines of text belong. There are also accounts that track the whereabouts of celebrities, like this one: (原帖链接Original post link: https://x.com/fs0c131y/status/1827828970856874115).
就寻找特定人员而言,虽然不能说百分百成功,但还算比较得心应手,例如想要联络到年少时的朋友对我来说不算是很困难。在几天前,我的一位好友兼学妹恳求我能否帮助她找到她童年时的伙伴,她说已经失去联络至少When 8it 年了,很思念这位伙伴。不过这位学妹也是早早地离开中国生活在海外,本来信息就很少,这么多年过去,很多事情都可能发生变化,那么我能最终帮助她找到嘛?comes to finding specific individuals, while I can't claim a 100% success rate, I can say I've become fairly adept at it. For instance, reconnecting with childhood friends isn’t particularly difficult for me. Just a few days ago, a friend and junior schoolmate of mine reached out, asking if I could help her locate a childhood companion. She mentioned that they had lost contact for at least eight years and that she deeply missed this friend.
However, this junior schoolmate had left China years ago and was now living overseas, and the available information was already limited. After so many years, countless things could have changed. So, was I ultimately able to help her find this long-lost friend?
嘛,之所以大家能看到我写的这篇文章,说明最终是找到了。寻找的过程中,我意识到这个寻找的经历是一个很好的素材,因为这些原因:Well, the fact that you're reading this article means I did eventually find her. During the search process, I realized this experience was a great case study for several reasons:
没有一步到位的捷径There was no shortcut that led directly to success.寻找难度适中The search presented a moderate level of difficulty.有曲折,但没有绝望的死路There were twists and turns, but no hopeless dead ends.涉及的技术具有多样性The techniques involved were diverse.存在多条可能的路径There were multiple potential paths to success.一些软技能与非技术手段能起到作用并节省时间Some soft skills and non-technical methods were crucial in saving time and effort.
以及,这个搜索最终让两个小姑娘在感动和温暖中重聚,而我也很有成就感,因为我用技术给她们带来了幸福和温暖。那么接下来,就从技术上分享一下这个过程。Ultimately, this search allowed two girls to reunite, bringing warmth and emotion, and I felt a strong sense of accomplishment knowing that my technical skills could bring happiness and comfort to their lives. Now, let's dive into the technical details of how this was done.
EliminatedRuled Out Shortcut
这位学妹告诉了我她童年伙伴的姓名和出生年份。尽管她们小时候在一起玩耍,但不一定意味着这位伙伴This junior schoolmate of mine provided me with the name and birth year of her childhood friend. Although they played together during their younger years, this doesn’t necessarily mean that her friend (下文都用referred ”目标“to 二字代替)的户籍就在本地,我的同学里就有好几位出生不久之后就来到了其他城市成长和生活。不过,暂且我先默认这位目标和我学妹的户籍相同,都在as **"the 市,如果无果再说。target" throughout the rest of this article) was registered locally. I know of several classmates who moved to different cities shortly after they were born. However, for the sake of convenience, I initially assumed that both my classmate and the target were registered in the same city. If that yielded no results, I would then consider other possibilities.
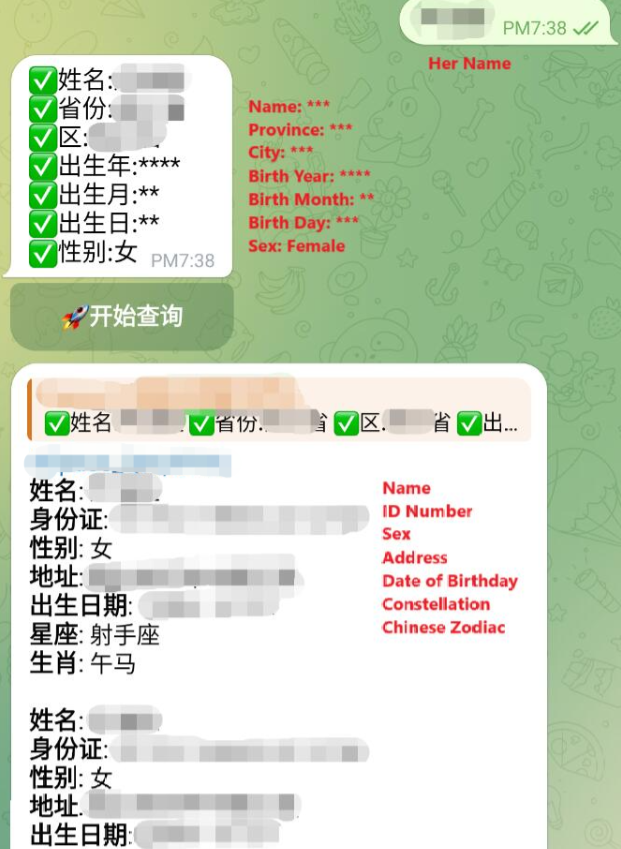
掌握了特定信息的话,如果运气好,最快速的方式是社工库。社工库是支持自定义查询,包含了过往泄露数据的数据库,往往在With Telegramsuch 上由自动回复机器人运行。根据查询的信息的详细程度,以及查询的次数,可能需要付费。需要注意的是,这些社工库是脱离政府管辖的黑灰产,并且有较多欺诈和骗子,需要格外谨慎。specific information, the quickest way, if lucky, would be to use a "social engineering library". These libraries support custom queries and contain past breached data, often operated by automated reply bots on Telegram. Depending on the detail of the search query and the number of searches, this may require payment. However, it’s important to note that these social engineering libraries exist outside of government control, part of the black or gray market, and are rife with fraud and scammers. Extra caution is needed.
除去数据陈旧之外,我发现这些社工库对以下情形效果不佳:Aside from outdated data, I’ve found that these social engineering libraries are not particularly effective in the following scenarios:
目标出生或者接触电子设备/互联网较晚The target was born or started using electronic devices/the internet later in life.目标早早地离开中国,或者移民其他国家了The target left China early on or immigrated to another country.目标十分注重隐私,或者很不热衷于各种AppThe target is highly privacy-conscious or avoids using various apps.目标年龄较大,不怎么使用电子设备The target is older and doesn’t frequently use electronic devices.改过名字,改过身份证,改过户籍等特殊情况The target has changed their name, ID, or household registration.
不管怎么样,根据已有信息,我在能确定的最小范围里尝试了查询,出现了几个同名的记录,但其他信息都不符合。因此,这条捷径就被排除了。但是,也并非没有留下任何信息,例如我得知了与目标重名的人并不多。因此,如果出生年份能对上,很大概率就是目标。Regardless, I proceeded to search within the smallest possible range using the information I had, and a few results with matching names appeared. Unfortunately, none of the other details lined up. So, this shortcut was ruled out. However, it wasn’t a complete dead end. I learned that people with the same name as the target were not very common. Therefore, if I could match the birth year, there was a good chance it would be the target.
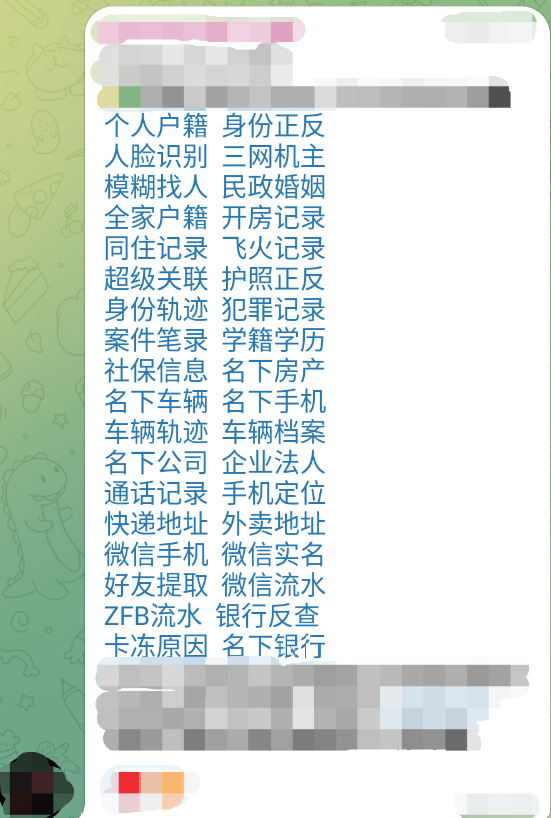
The following screenshot is from a Telegram channel, and while I haven’t annotated the English translation in the image, it serves as an example of the types of services offered by the admin. They can provide household registration details, phone number lookups, facial recognition, ID card images, marriage information, hotel booking records, and more.
The Power of Google Dorking and Keyword Pivoting
既然没有捷径的话,那么我们就脚踏实地地进行搜索与分析。这里,谷歌Since there were no shortcuts, we proceeded with a methodical search and analysis. In this case, Google Dorking 派上了很大的用途。我没有直接只搜索目标的名字,而是加上了她当时所在的城市,并且强制要求城市名出现在网页中。proved extremely useful. Instead of simply searching for the target’s name, I included the city where she used to live and made sure the city name had to appear on the web pages.
intext:"<城市名>" <目标姓名>经过筛选,我得到了如下After 2filtering 个疑似相关的记录:through the results, I found two potentially relevant records:
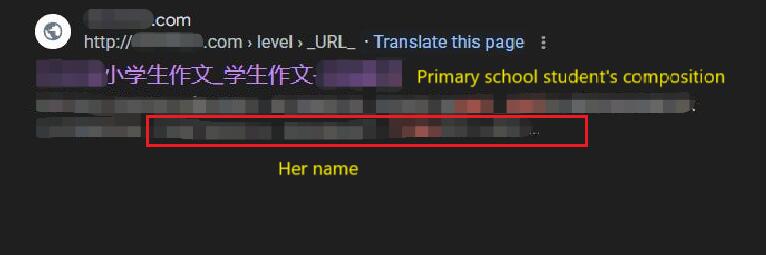
第一个记录疑似是目标小学时候发表的作文,被搜集在这个网站上。第二个记录疑似是目标当前所在大学发布的关于英语竞赛考场分布的文档,里面包含了参赛考生的名字,学生ID(此时还尚未确认),座位编号等。The first record seemed to be an article written by the target during primary school, which had been collected on a website. The second record appeared to be a document from the university where the target might be studying, listing the seating arrangements for an English contest. It included the participants' names, student IDs (though this was yet to be confirmed at this point), and seat numbers.
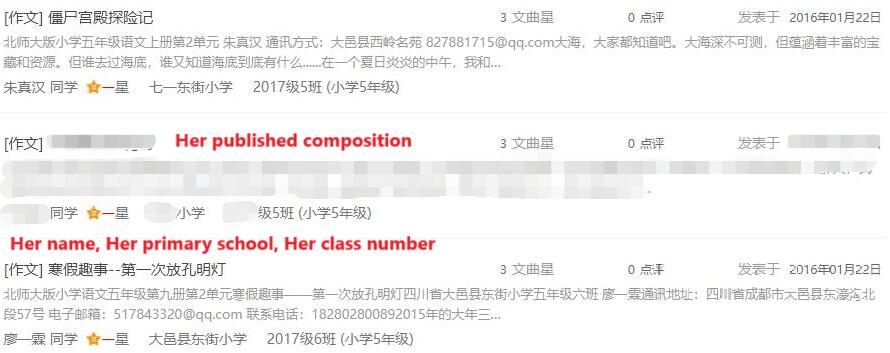
不管怎样,先访问第一个记录看看,能看到目标的名字,当时所在小学,小学毕业年份和班级。经过计算,目标确实应该在这年小学毕业,时间对的上。考虑到与目标重名的人很少,那么这个作文确实是目标小学时发表的了。First, I checked the article. It mentioned the target's name, her primary school, the year of her graduation, and her class. After calculating, the target would indeed have graduated from primary school in that year, so the timing matched. Given that the name isn’t common, this article was likely written by the target during her primary school years.
然后,我准备访问第二个记录,发现网页加载不出来。搜索记录页面的预览内容应该是缓存的,不过好在我至少知道目标可能就读的大学了。考虑到第二个记录并不是学校官方发布的,那么很可能是转载的,也意味着学校官网肯定发布过这个公告。Next, I attempted to access the second record, but the webpage wouldn’t load. The preview content of the search results was likely cached, but fortunately, I at least had a clue about the university where the target might be studying. Since the second record wasn’t an official school release, it was likely a repost, which meant the university's official website probably had the original announcement.
于是,我调整So, I adjusted my Dorking 语句,以她可能就读的学校为新的关键字,搜索语句如下:query, using the potential university as a new keyword. The search query was as follows:
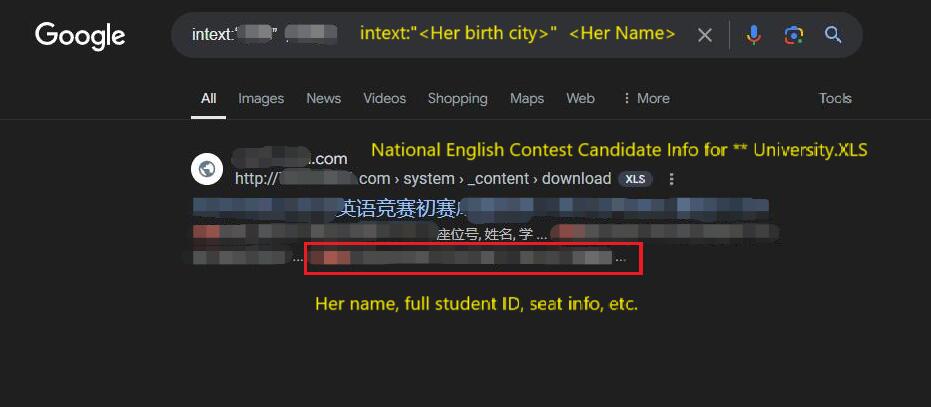
intext:"<目标可能所在学校>" <目标姓名>果然在官网找到了关于该英语竞赛的公告。Sure enough, I found the official announcement about the English contest on the university’s website.
在该公告里,有着考场分布信息的In the announcement, there was an XLS 文档,里面包含了考生的相关信息,以及疑似目标的学生信息,包括姓名,完整学号。document containing exam room distribution information, which included relevant details about the participants, as well as the suspected target’s full name and student ID.
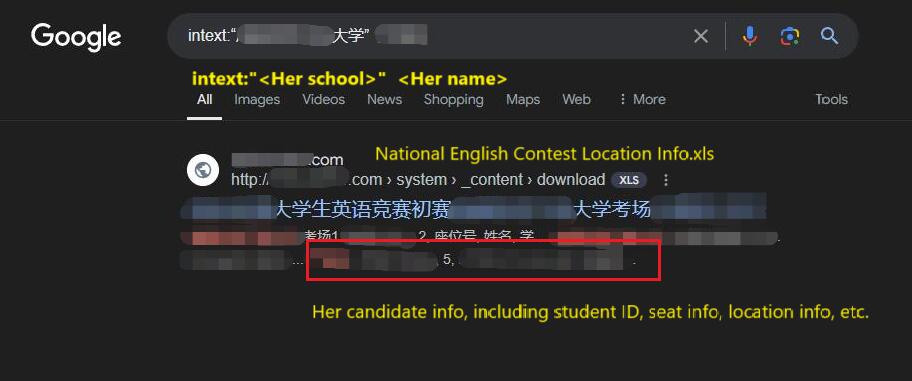
虽然我觉得很大概率就是目标,但我想获得更多证据。于是,我调整了搜索语句,如下:Although I was fairly confident this was the target, I wanted more evidence. So, I adjusted my search query as follows:
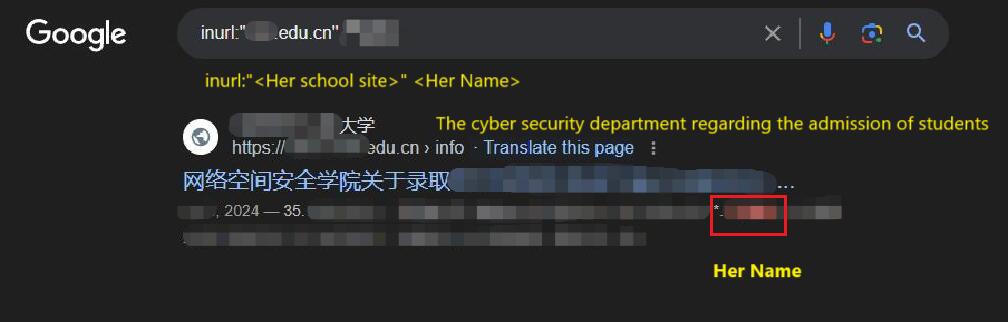
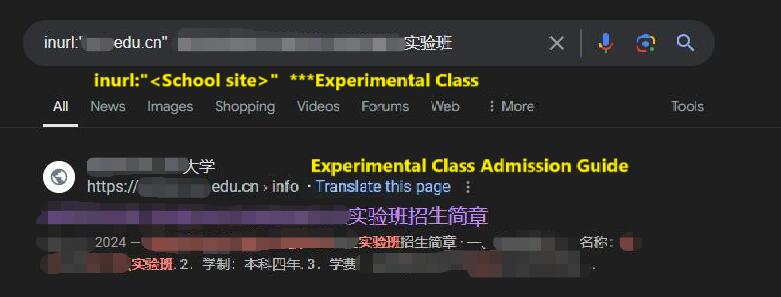
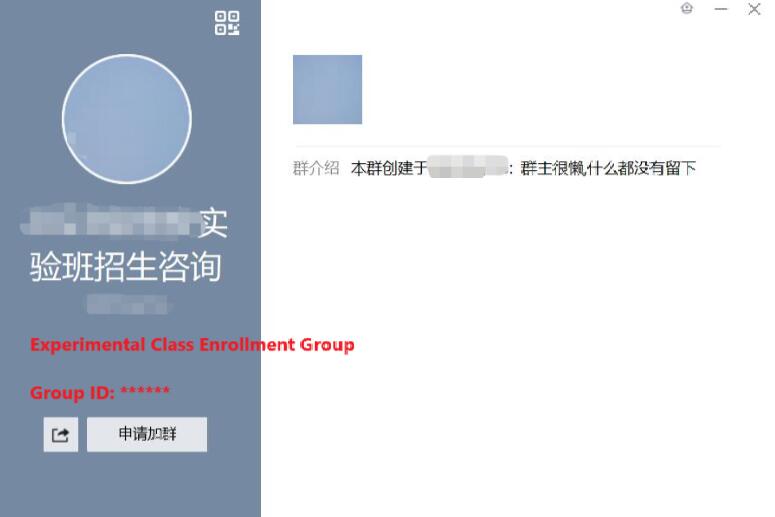
inurl:"<xxx.edu.cn>" <目标姓名>我得到了如图所示的一个记录,这是该校网络安全学院发布的关于实验班的录取通知,包含了目标的名字。到这里的时候,我有些震惊和兴奋,因为我自己就是网络安全从业者,没想到我正在搜索的人可能是行业里的后辈。I came across a record, as shown in the image, from the university’s cybersecurity department, announcing the admission of students into an experimental class, and it included the target’s name. At this point, I was both shocked and excited because, as a cybersecurity professional myself, I hadn't expected the person I was searching for might actually be a fellow member of the industry, possibly one of the next generation of professionals.
点进去之后,我看到了这批学生,当然也包括目标的入学年份。根据她的出生年份以及小学毕业年份做了简单计算,这个大学入学年份是吻合的。以及因为重名者很少,那么基本可以断定就是目标了。After clicking on the link, I confirmed the batch of students, including the target, along with their enrollment year. By doing some simple calculations based on the target’s birth year and primary school graduation year, I verified that the university enrollment year matched. Considering how uncommon the target’s name was, I was now almost certain that this was the person we were looking for.
现在,我们得知了以下这些信息:At this point, we had gathered the following information:
目标在当地的一小学就读并毕业了The target attended and graduated from a local primary school.目标在当地的一大学就读网络安全专业,属于实验班The target is currently studying cybersecurity at a local university, enrolled in an experimental class.目标在该大学参与过英语竞赛The target participated in an English contest at the university.
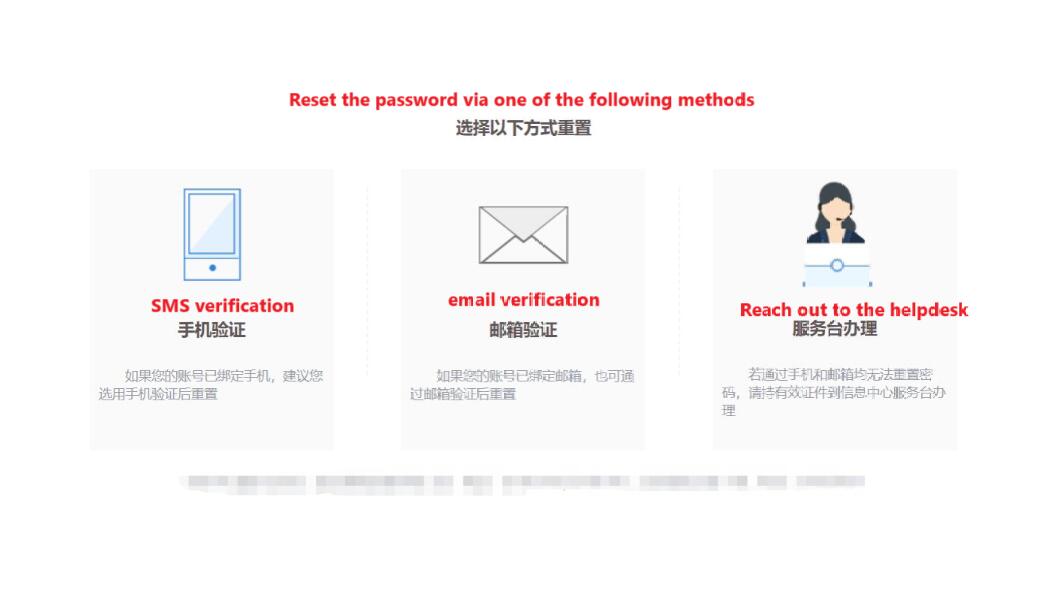
我们知道了目标的学号,和所在大学,并且大学网站往往都有学生登录入口。我想着,能否从学生登录入口找到存在于响应和报错中的更多信息。如下图所示,因为我不知道目标的密码,那么能否通过密码重置功能得到目标手机号的信息呢?We now had the target’s student ID and the university she attended, and university websites typically have a student login portal. I wondered if I could uncover more information through this portal, perhaps by analyzing the responses or error messages. As shown in the image, since I didn’t know the target’s password, I considered whether the "password reset" function might reveal further details, such as the target’s phone number, during the process.
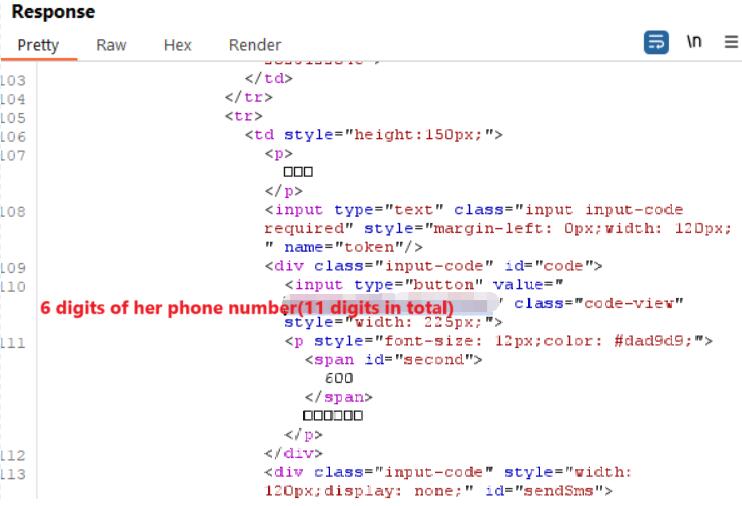
从响应中,我确实得到了目标的手机号码,但只是其中From the response, I did indeed retrieve the target's phone number, but only 6 位,开头digits were visible—3 at the beginning and 3 位和结尾at 3the 位,中间还有end—leaving 5 位,即最多unknown 99999digits 种可能。in the middle, resulting in up to 99,999 possible combinations.
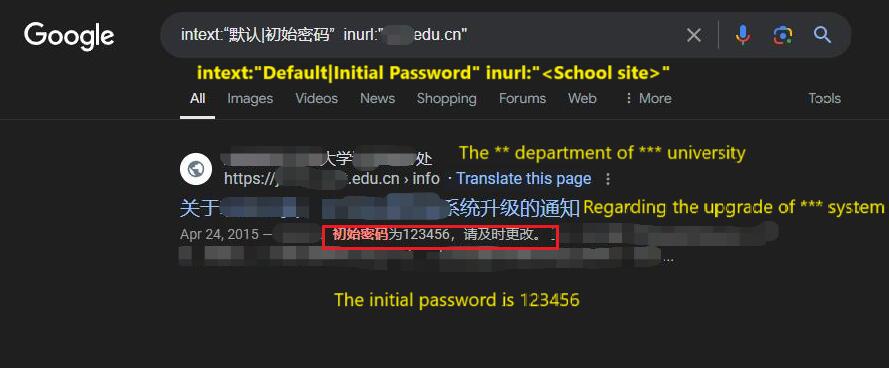
我抱着试一试的态度,看看能否从校内站点找到包含默认密码的相关文档:I decided to take a chance and see if I could find any internal documentation on the university’s site that might contain default passwords for student accounts:
intext:"<默认|初始密码>" inurl:"xxx.edu.cn"还真找到一个记录,得知所有学生账号的初始密码是Sure 123456,但我觉得目标这种选择网络安全专业的学生肯定会早早修改了,事实也是如此。enough, I found a record stating that the initial password for all student accounts was “123456.” However, given that the target was a cybersecurity student, I figured she would have changed this password early on, and indeed, she had.
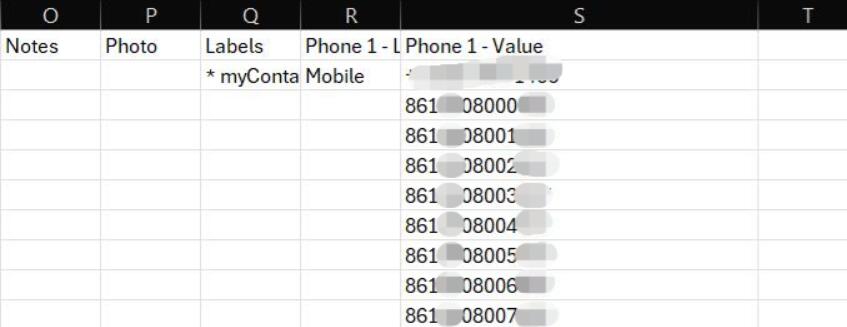
这样的话,意味着得到手机号码也没有捷径了,因为有This meant there was no shortcut to obtaining the full phone number, as I still had 5 位未知,那么最多missing 99999digits, 种可能。但实际上,手机号码具有一定规律性,而不是随机的。根据目标所在地区,筛选后只剩下leaving 2400up 个可能号码了。虽然依旧不是很方便手动筛选,但可行多了。to 99,999 possible combinations. However, phone numbers follow certain patterns rather than being random. By filtering based on the target's region, I managed to narrow it down to 2,400 possible numbers. While still not ideal for manual testing, this was much more feasible.
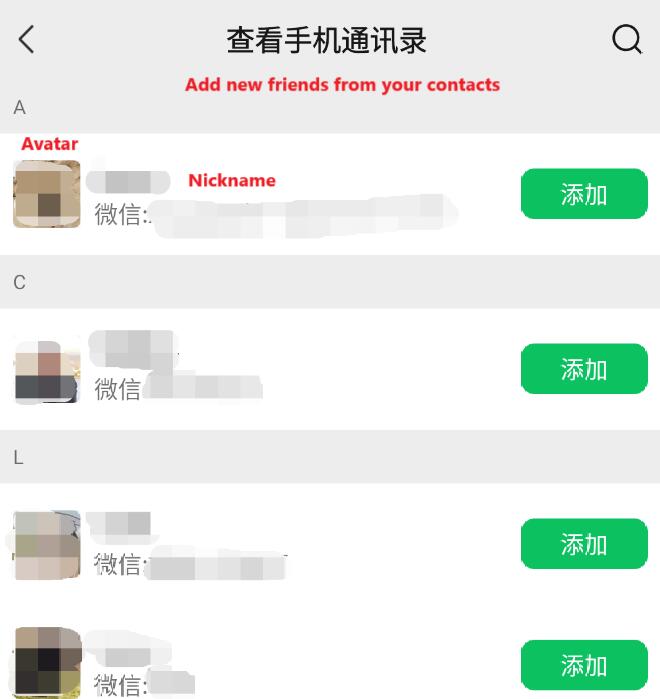
我创建了新的I created a new Google 账号,并把这些可能的号码创建为account 2400and 个联系人,导入到added the 2,400 possible phone numbers as contacts. Then, I imported them into Google 通讯录中,并同步到手机本地。无论是中国还是海外的Contacts App,大都支持从通讯录添加好友。根据应用的不同,我们可能得知号码所关联账号的真实姓名,头像,Bio,生日,等个人资料。例如微信,可以显示号码关联账户的头像,昵称,Bio。支付宝可以显示关联账户的真实性别,部分姓名。and synced them to my phone. Many apps, whether in China or other regions, support adding friends from the contact list. Depending on the app, we might be able to gather additional personal information linked to those numbers, such as the real name, profile picture, bio, or even birthday.
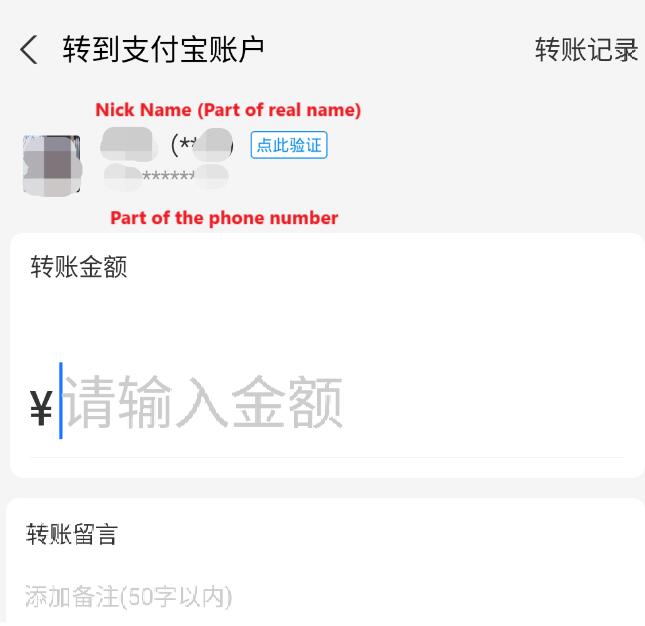
For example, on WeChat, you can view the avatar, nickname, and bio of the account linked to a phone number. Alipay, on the other hand, can display the real gender and part of the person's name associated with the account. By cross-referencing this information with the details we already knew, I could potentially identify the target's correct number and profile.
不过,即便如此,依旧需要一定的工作量。而且,不幸的是,支付宝已经意识到这样的健全性检查的利用,在我查看了一些号码的真实姓名后,便阻止了我使用此功能。However, even with this approach, there was still a considerable amount of manual work involved. Unfortunately, after checking the real names linked to some of the numbers on Alipay, the platform realized what I was doing and restricted my access to that feature.
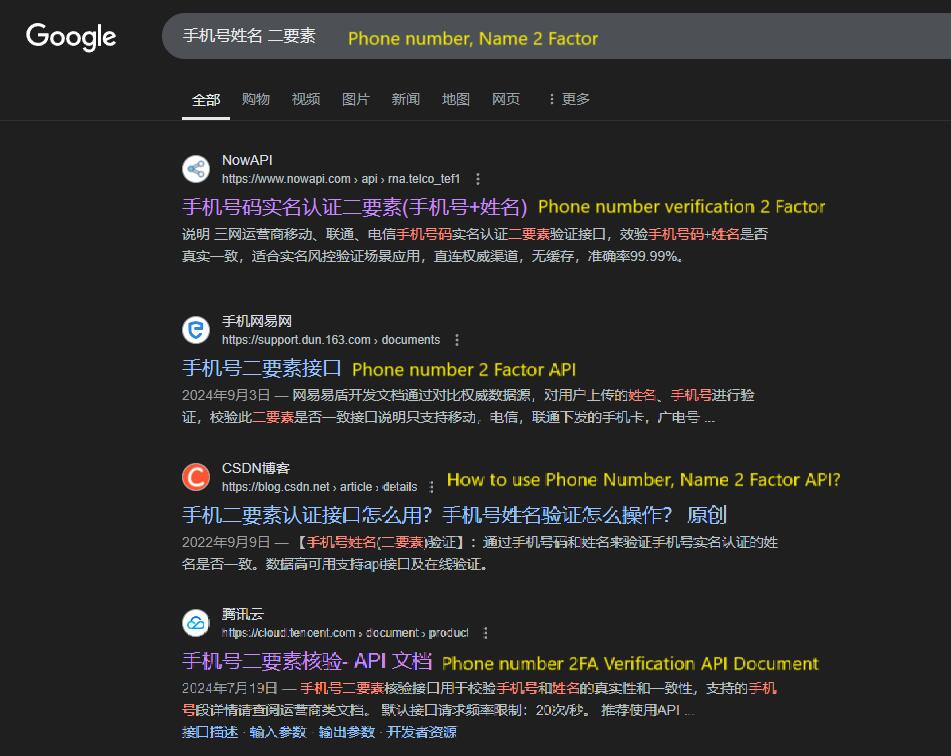
但这没有关系,AppHowever, 对手机号关联检测的背后是this APIwasn’t 的运作,我们甚至不需要微信和支付宝这样的应用,而是直接调用手机号与姓名的二要素验证a API。通过在谷歌上搜索,我们能看到一些厂商提供这样的major API。setback. The underlying process of linking phone numbers with accounts on apps like WeChat and Alipay is managed through APIs. We don’t necessarily need to use the apps themselves. Instead, we can directly leverage APIs that perform two-factor verification, such as checking a phone number against a name. By searching on Google, I found some providers that offer such APIs, which can automate and expedite the process of verifying the correct number and identifying the target more efficiently.
但不幸的是,尽管理论可行,调用这些Unfortunately, APIwhile 前往往需要严格的身份验证,而我长年不在中国,没有可用于绑定的中国手机号。并且,这些接口并非与中国公民数据库对接,而是各个厂商自己的实现,数据池大小不一。this approach was theoretically feasible, using those APIs often requires strict identity verification, and having lived abroad for many years, I no longer had a valid Chinese phone number to link. Moreover, these APIs don’t directly interface with Chinese citizen databases; instead, they rely on data collected by various companies, meaning the data pool can vary significantly in size and accuracy.
当然,只要多等一些天,凭借目前的这些信息足以能将目标找到。接下来,我“作弊”了一下,但请先别生气,因为我在下个部分会介绍其他的路径。我帮学妹找人,不是为了证明什么,而是想尽早让她们团聚,仅此而已。Of course, with some patience, the information we had at this point would have been sufficient to locate the target eventually. But I did take a little "shortcut" here—don’t be upset! I’ll explain alternative methods in the next section. My goal in helping my junior schoolmate wasn’t to prove anything, but simply to reunite them as soon as possible.
目标是网络安全专业的学生,而且她所在的学校还是比较令人耳熟的,我想到网络安全社区的学生整体来说都比较活跃,他们可能活跃于Since CTF,可能活跃于the Bugtarget Bountywas 挖洞,可能活跃于博客等。以及,我是一位有一定观众数量的内容创作者,于是我就在自己所主持的社区里问了问有没有同在目标学校的,还真遇到了!后来,经过一些传话和解释,在目标的同意下,得到了她的联系方式,我也分享给了学妹,她们圆满地团聚啦。a cybersecurity student at a fairly well-known university, I realized that students in this field are often quite active in the cybersecurity community. They may participate in CTF competitions, engage in bug bounty programs, or run personal blogs. Additionally, I’m a content creator with a decent following, so I decided to ask around in the community I manage if anyone was attending the same university as the target.
Sure enough, I found someone! After some communication and explanation, and with the target’s consent, I was able to get her contact details. I passed the information along to my classmate, and the two of them were happily reunited.
Alternative Paths
大家看到这里,可能会觉得有些虎头蛇尾,毕竟最后一步并不是我靠At this point, some readers might feel that the conclusion is somewhat anticlimactic, as the final step didn’t rely solely on OSINT 技术实现地。好在我在复盘的时候,发现了其他的路线,接下来我来展示一下。techniques. However, during my review of the process, I discovered other potential avenues, which I'll now share.
在英语竞赛的通知中,我发现了用于报名的In the English contest announcement, I noticed a QQ 群,以及负责老师的联系方式。group used for enrollment, as well as the contact information of the responsible staff.
This opened up new possibilities for gathering further information. For example, by joining the QQ group or reaching out to the teacher, I could have explored the participants' details or even contacted the target directly. These additional pathways also demonstrate how OSINT techniques can involve leveraging social and professional networks, not just technical methods.
以及,通过如下的语句可以找到目标学校关于实验班的招生简章:Additionally, by using the following dorking, I was able to find the admissions guide for the experimental class at the target’s university:
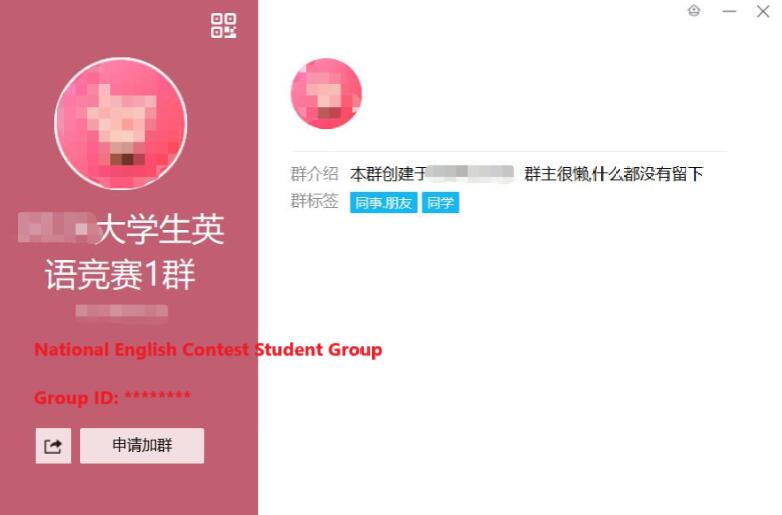
inurl:"xx.edu.cn" <***实验班>点进去,我找到了用于咨询的Upon further investigation, I found a QQ 群:group listed for inquiries:
后来,经过确认,目标说她确实在这两个群里。那么,即便没有那位人脉的帮忙,我可以通过加入到这两个群里进行筛选从而找到目标的联系方式。Later, after confirming with the target, she mentioned that she was indeed part of these two QQ groups. This means that even without the help of personal connections, I could have joined these groups and filtered through the members to locate the target’s contact information.
This demonstrates another potential path that could have been taken, using group memberships and social platforms as part of an OSINT investigation to reconnect with the target. It’s a reminder that sometimes, even simple social methods can be as effective as technical approaches in achieving the desired outcome.
Summary
总之,在没有泄露数据这条捷径的帮助下,我凭借目标的姓名和出生年份这In 2conclusion, 条信息,找到了学妹失去联络without relying on shortcuts like leaked data, I was able to locate my junior schoolmate’s childhood friend, whom she had lost contact with for over 8 年以上的童年伙伴。与学妹的交流中我感受到她真的很想念这位伙伴,以及珍惜两人小时候的友情。在她们俩圆满团圆后,也不停跟我说觉得这一切很不真实,哈哈。years, using just two pieces of information: the target’s name and birth year. Throughout my conversations with my junior schoolmate, I could sense how much she missed this friend and cherished their childhood friendship. After they were finally reunited, she kept telling me how surreal it all felt, which made me laugh.
这位目标有些惭愧地跟我说觉得自己没有很好地保护好自己的网络痕迹,但其实她并没有什么The target, on the other hand, somewhat sheepishly remarked that she hadn't done a good job protecting her online footprint. But in reality, she hadn’t made any significant OPSEC 和隐私上的失误。小学时发表一篇作文这很正常与合理,反而是她所在的大学透露了不少她的近期活动。or privacy mistakes. Publishing an essay during elementary school is completely normal and reasonable. In fact, it was more her university that inadvertently revealed quite a bit about her recent activities.
利用Using OSINT 技术寻找失去联络的朋友,对于我来说并非第一次,也有更加曲折和困难但最终成功的经历。但技术之外,这绝对是让我最印象深刻的一次了,因为让我意识到我的技术,网络安全技术,也能带来温暖和人情味。techniques to find lost friends isn’t new to me, and I’ve had other experiences that were more complex and challenging but still ultimately successful. However, this case left the deepest impression on me, because it made me realize that cybersecurity skills, often seen as technical and impersonal, can also bring warmth and human connection.